This topic describes what Folder security profiles are and how to manage them in the Folder security section of the System Administration.
By default, users of a Board Platform can access all the Capsule folders on that Platform. However, there are cases where a company may have different applications made of various Capsules on the same Platform, such as a financial planning application and a sales operations application. In addition, there may be administration Capsules for both applications as well. Therefore, access to these Capsules should be controlled according to the role of each user, especially for administrative roles. In this scenario, you can place the Capsules of the various applications inside different Capsule folders, and then create Folder security profiles to allow users access only to certain Capsule folders. Finally, assign these Folder security profiles to the desired user Roles in the Roles section to grant users associated with those Roles access to different Capsule folders.
Folder security profiles represent the third security layer of Board's Four Security Layers model.
To access the Folder security section, open the System Administration area of the desired Platform and click on the Folder security tile.
In the Folder security page you can see all existing Folder security profiles and their main information: the table is sortable and searchable using the interactive header fields. You can also show or hide columns to your liking by clicking the Column chooser button in the upper right corner of the table.
The table contains the following information:
Name. This column displays the name of each Folder security profile.
Creating a Folder security profile
To create a Folder security profile, proceed as follows:
From the Folder security section of the desired Platform, click the (
 ) button next to the Folder security title in the upper left corner to bring up the Folder security profile configuration panel
) button next to the Folder security title in the upper left corner to bring up the Folder security profile configuration panelEnter the name of the Folder security profile in the "Name" field.
Configure the Access level for each Capsule folder. Under the "Folder security" section, you can configure the access level for any Capsule folder in the table below to further specify the type of actions a user can perform in the Capsules accessible to them.
The available options are the following:Play only. This option allows users associated with this Folder security profile to access a Capsule folder and its content in Play Mode only: this means that users cannot edit the Capsules inside of the Capsule folder and cannot switch to Design Mode.
Read only. This option allows users associated with this Folder security profile to access a Capsule folder and its content in Read Mode only: this means that users cannot edit the Capsules inside the Capsule folder, but they can switch to Design Mode, but without the rights to save any changes that they make while designing.
Read & Write. This option grants users complete access to a Capsule folder and its content: this means that they can create and edit Capsules inside that Capsule folder.
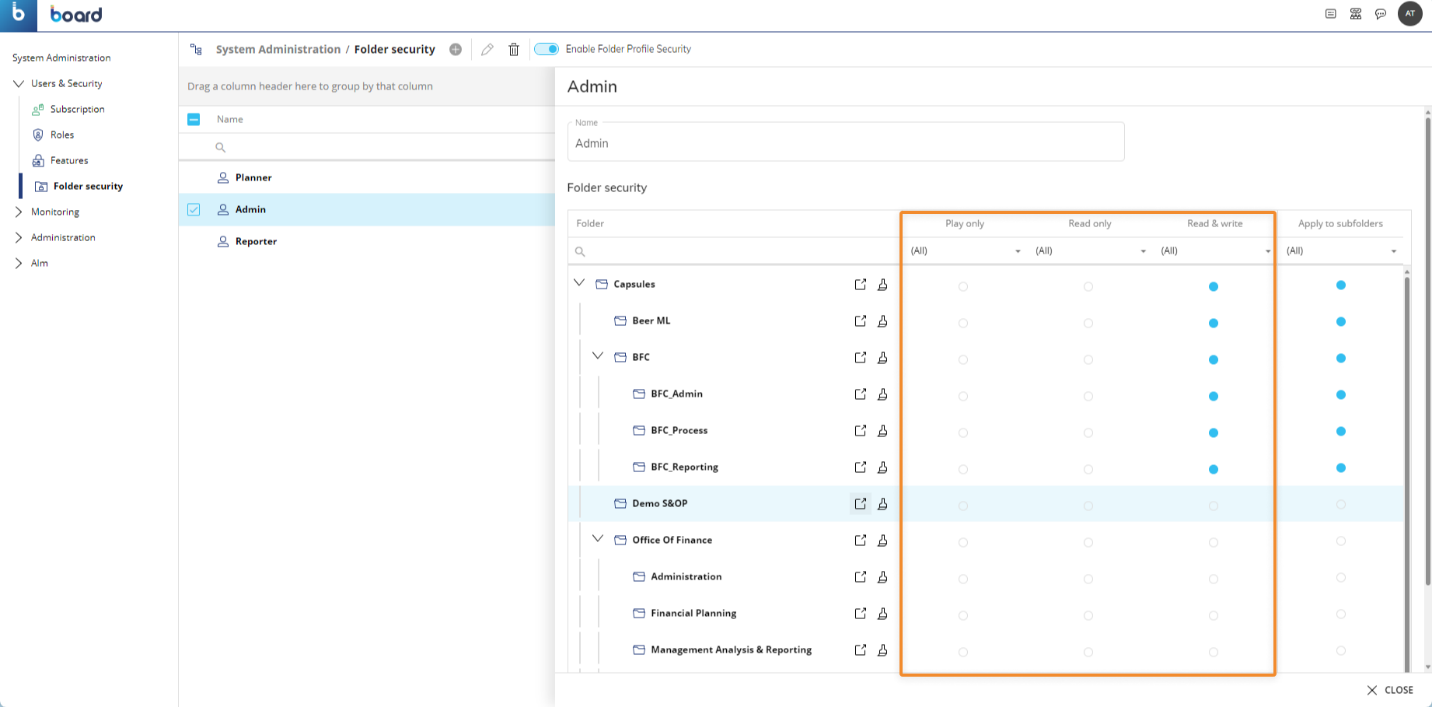
Only Capsule folders displayed in the table with a configuration can be accessed by users associated with the corresponding Folder security profile.
(Optional) Apply to subfolders. If enabled, the access level defined for the Capsule folder will be applied to all its subfolders. For example, if there is a Capsule folder named "Parent" that contains a Capsule folder named "Child" and you create a Folder security profile that allows access to the "Parent" Capsule, then the user will be able to access only the "Parent" folder and not the "Child" folder if the "Apply to subfolders" option is not selected.
If you create a security rule that allows a user access to a subfolder, but there's no security rule that allows that user access to the parent folder, the user will be able to access the parent folder in "Play only" mode by default.
Managing and assigning Folder security profiles
To edit a Folder security profile, select it and click the pencil icon to modify the desired options as explained in the steps above.
To delete one or more Folder security profiles, select the desired ones and then click on the trash icon in the top left corner.
To associate one or more Folder security profiles with a user Role:
Click on the "Enable Folder Profile Security" toggle to enable the Folder security feature.
If this option is disabled, Folder security profiles cannot be associated with users and therefore will not be applied.
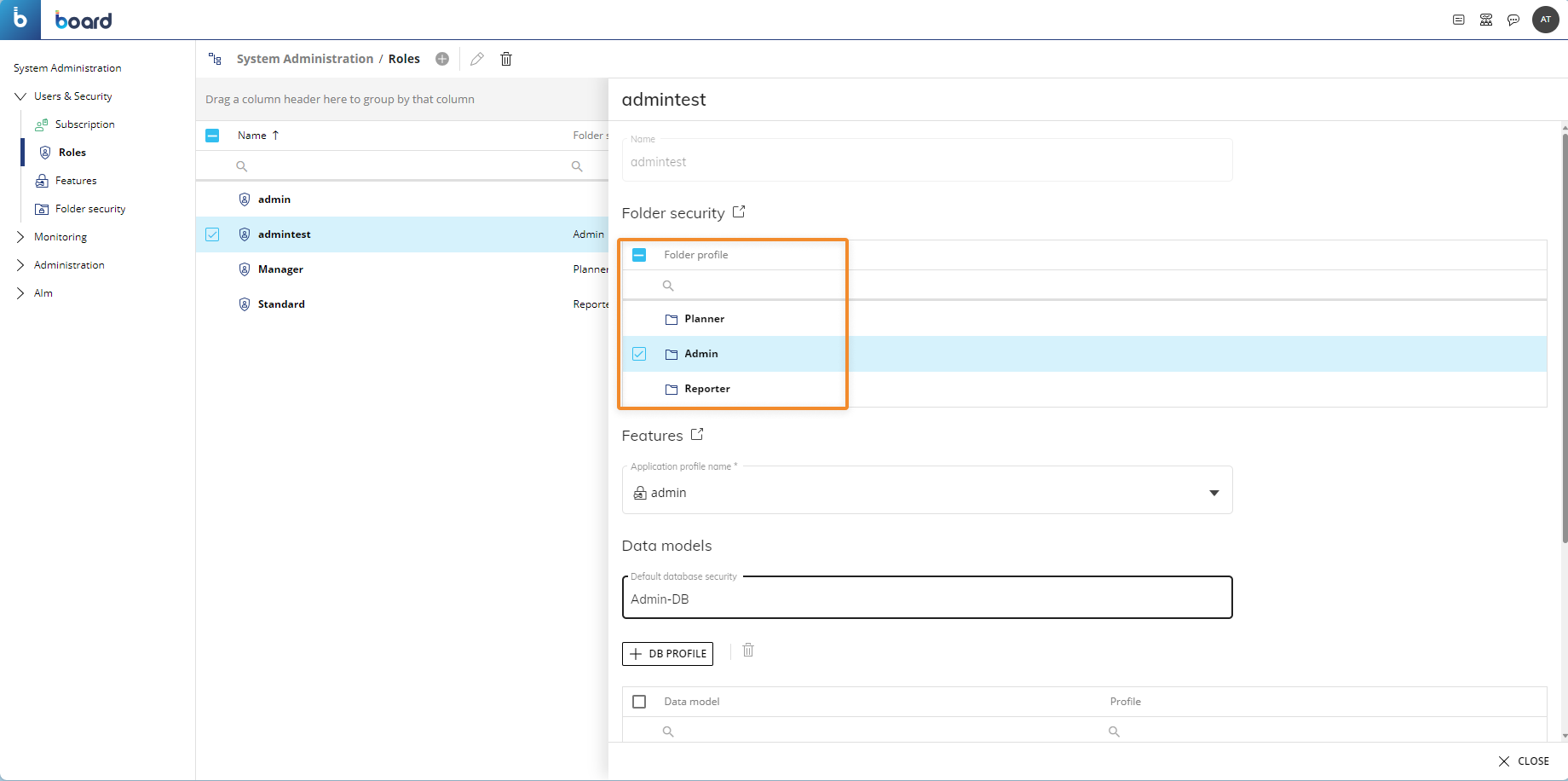
In the System Administration area, go to the Roles section and select the Role you want to assign a Folder security profile to.
Check the corresponding checkboxes to enable the desired Folder security profiles under the "Folder security" section.
In the case of a Role associated with multiple Folder security profiles that have overlapping security rules (i.e. different access levels for the same Capsule folder), the rules with higher privileges will take precedence over the others.
Folder security profiles with overlapping security rules
Board allows you to assign multiple Folder security profiles to a single Role. In this case, a user associated with that Role is able to access Capsule folders that are referenced in at least one of the security rules of all Folder security profiles assigned to that Role. In the case where some of these security rules apply to the same Capsule folder, Board considers the one with the highest access level.
The access level hierarchy, from highest to lowest privileges, is the following:
Read & Write (highest privileges)
Read only
Play only (lowest privileges)
For example, you can create two Capsule folders named "HR Admin" and "HR Local" with additional subfolders in them. Then you can create two Folder security profiles named "Developer" and "Standard" and create the following security rules:
Developer. This Folder security profile can access both the "HR Admin" and "HR Local" Capsule folders with the "Read & Write" access level. In addition, you can enable the "Apply to subfolders" option on both security rules, which gives the user "Read & Write" access to all the subfolders of the two Capsule folders.
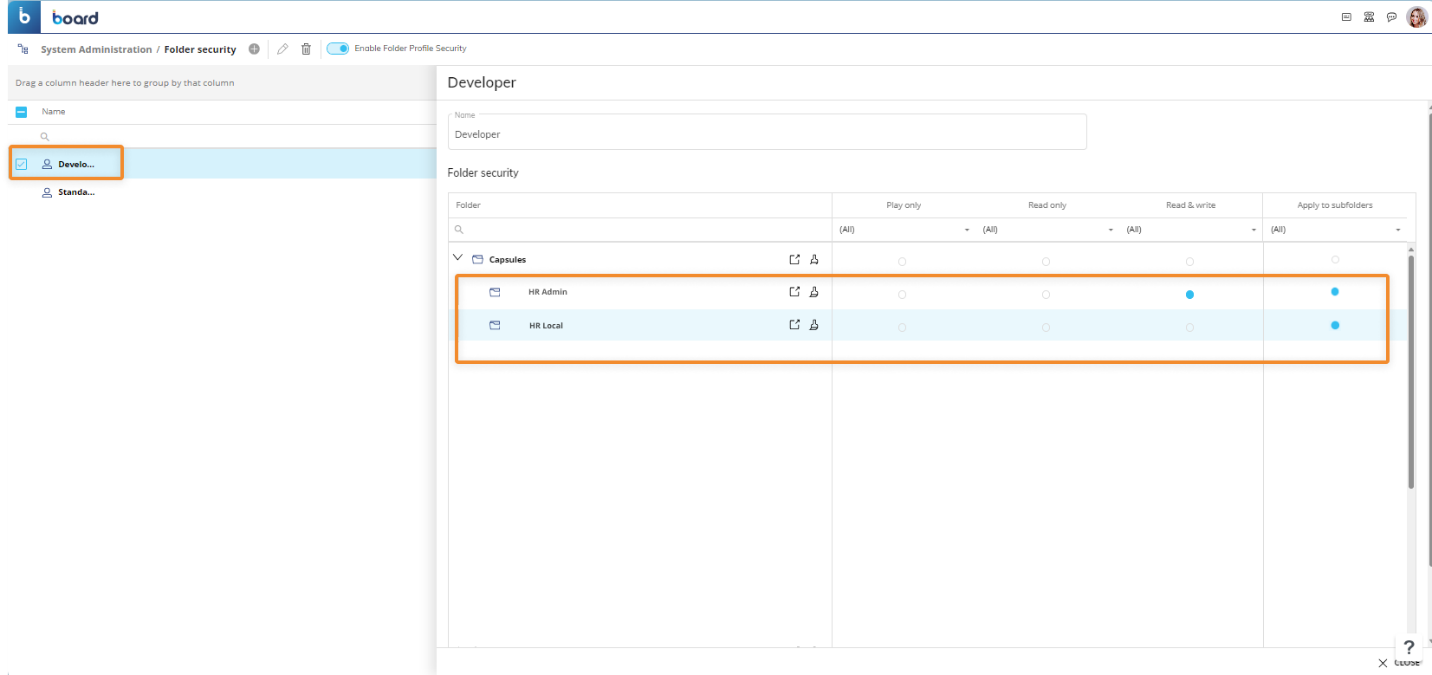
Standard Local. This Folder security profile can only access a specific subfolder of the "HR Local" Capsule folder named "HR Italy" with the "Play only" access level.
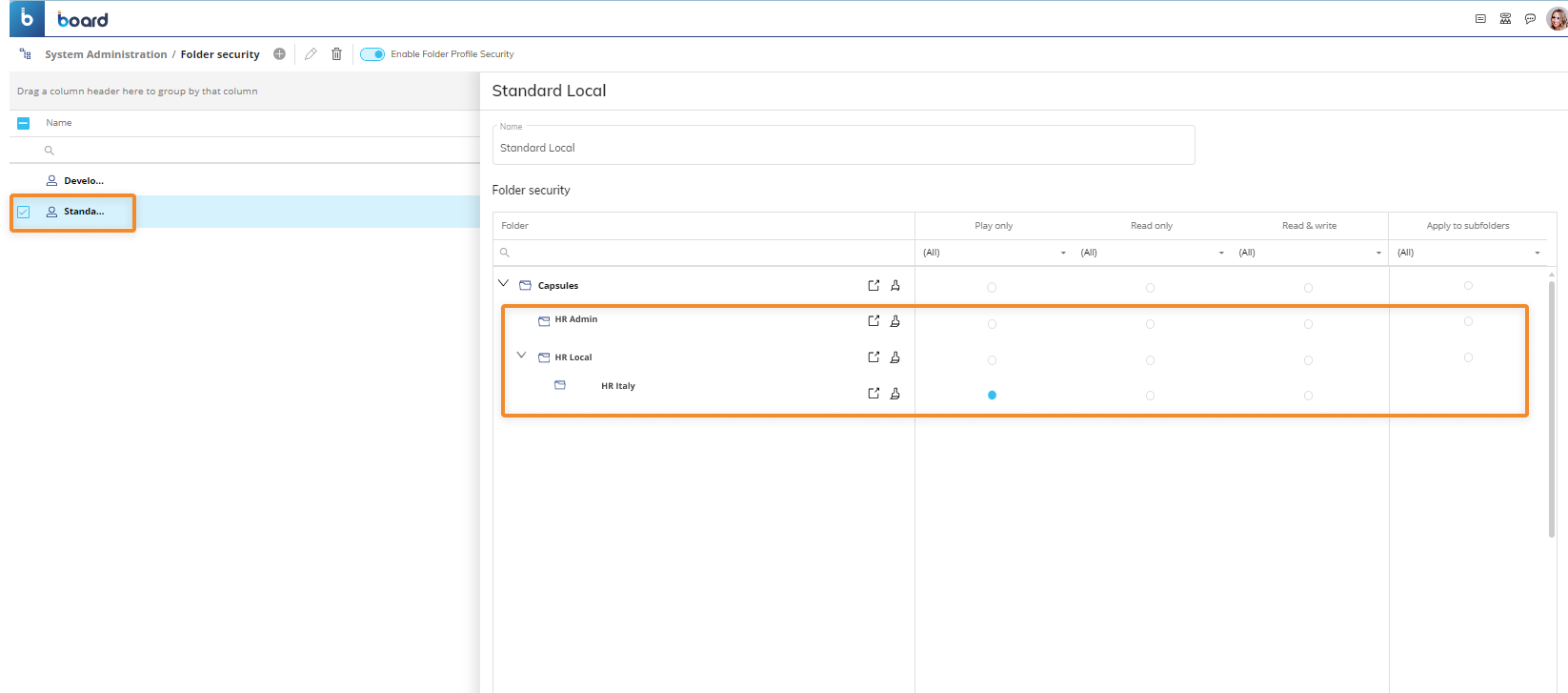
At this point, you can assign both Folder security profiles to a Role named "Admin", and then assign only the "Standard Local" Folder security profile to a Role named "Standard", as shown in the two images below:
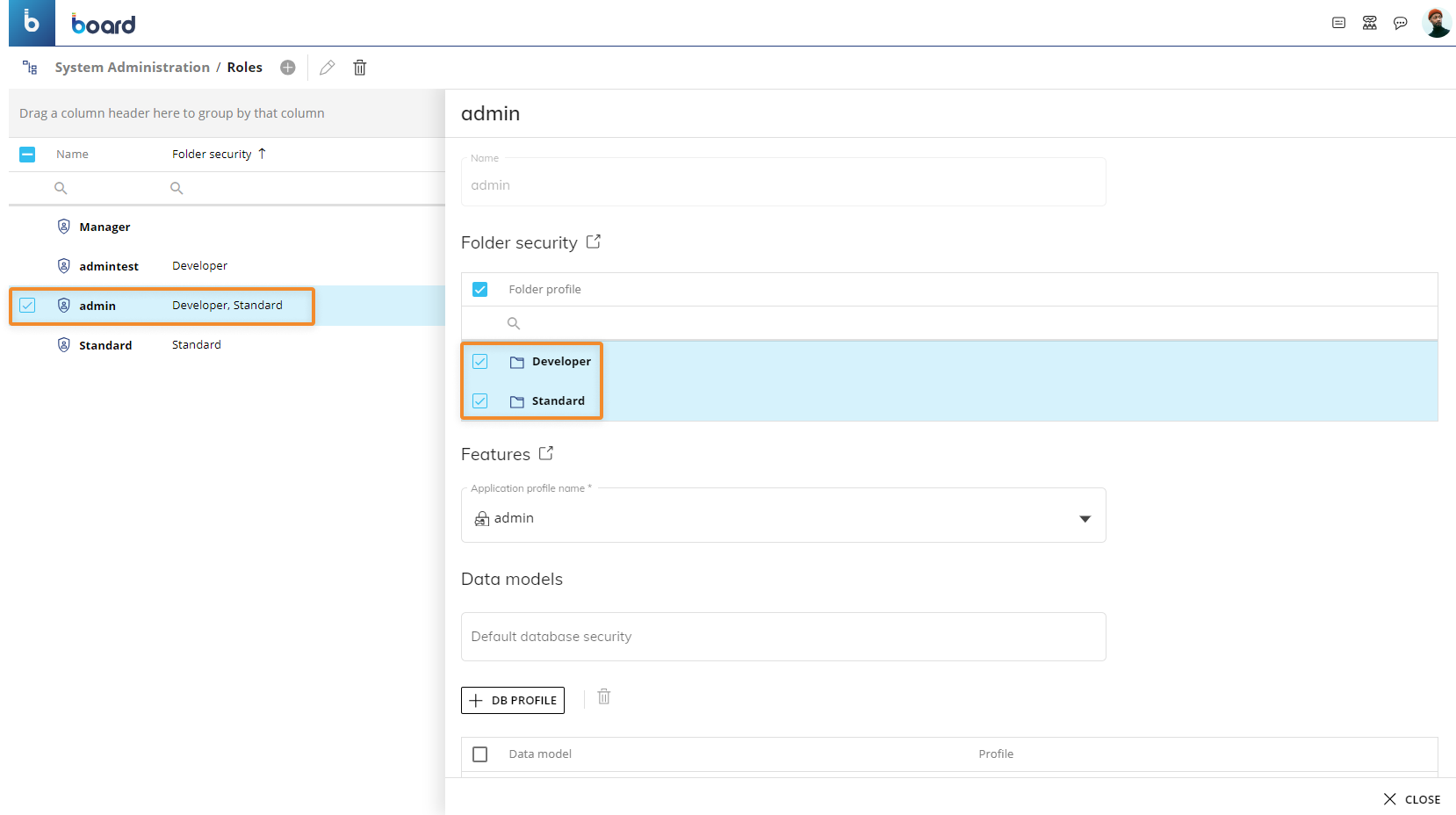
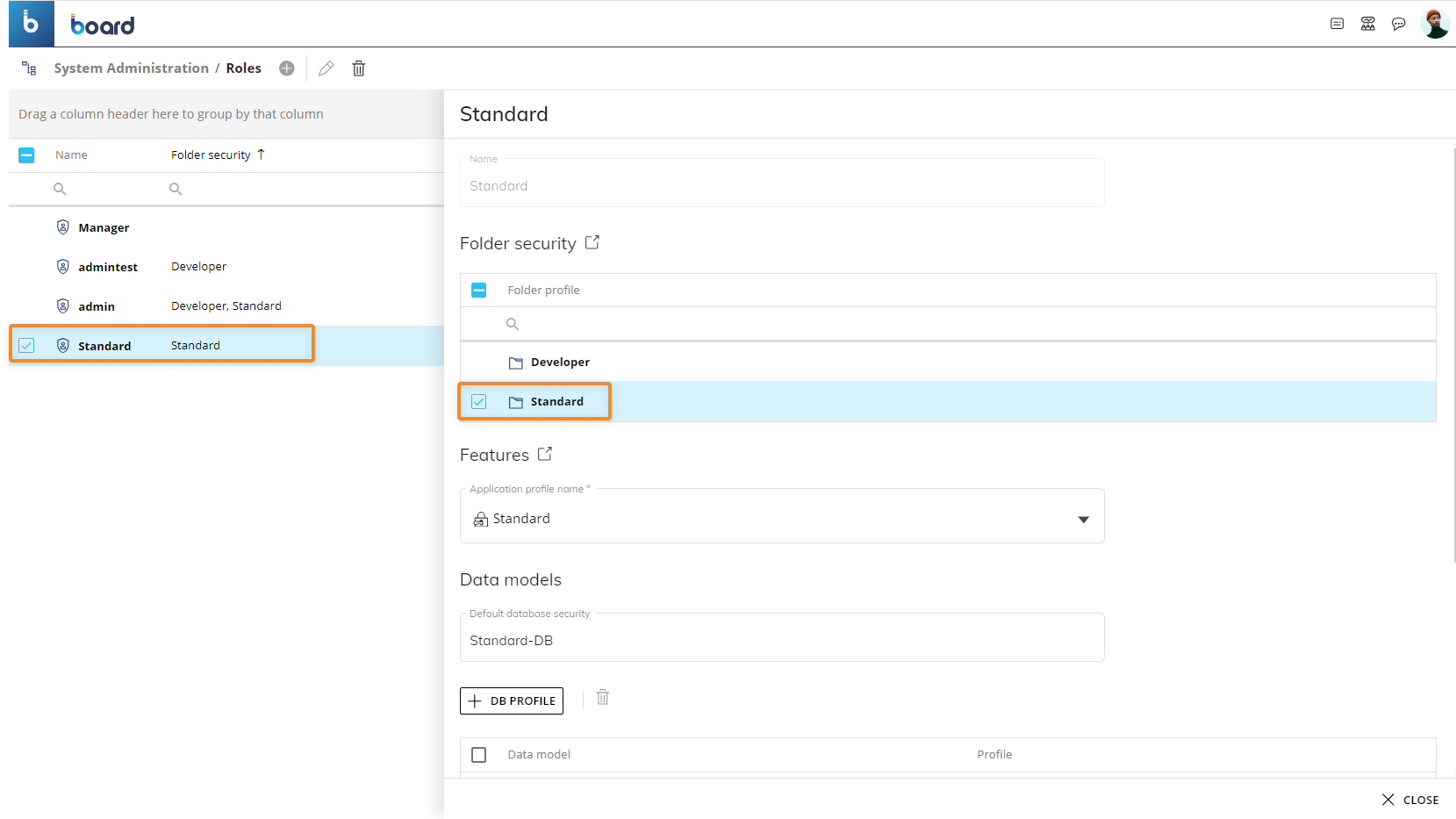
In this case, Board applies the security rules of the Folder security profiles for both Roles in the following way:
Users associated with the "Standard" Role are only able to access the "HR Local" Capsule folder and its "HR Italy" subfolder with "Play Only" access level.
Users associated with the "Admin" Role are able to access the "HR Admin" and "HR Local" Capsule folders with "Read/Write" access level. They can also access the subfolders of those Capsule folders (including the "HR Italy" subfolder) with the same "Read/Write" access level since the "Apply to subfolders" option is enabled in the security rules of the "Developer" Folder security profile.
Therefore, in the case of the users associated with the "Admin" role, Board applies all security rules in both Folder security profiles, and in the case where security rules overlap, those with the highest access level take precedence over the others.